In this article we will examine password recovery process for Cisco devices. Sometimes you can forget the passwords and need a recovery. Or may be you are a hacker and you may want to break the device's password 🙂 Whatever, it is time to take a look for the process. In this article I will tell you how you can recover the password of Cisco 2600 or 2800 series routers.
First of all, you need a console cable and software for serial connection ( like Putty ). Plug the console cable to console port and choose 'serial' connection on Putty. Select the COM port that your computer using correctly and click 'connect'. When your serial connection is made correctly, power off the cisco device and turn it on again. After you need to press 'break' button on your keyboard and go to the rommon mode ! Here are the next steps :
- Type confreg 0x2142
- Type 'reset'
- Type 'no'
- Type 'enable'
- Type 'copy startup-config running-config'
- Type 'configure terminal'
- Type 'enable secret ' // like 'enable secret myhardpassword'
- Type 'config-register ' // like 'config-register 0x2102'
- Type 'write memory'
Because there is only one console port per router, you would use the command line console 0 in global configuration mode, and then use the login and password commands to finish up the. Telnet scanning with Cisco Torch will identify telnetd running on nonrouter Cisco machines, such as Catalyst switches and PIX firewalls. The addresses of found Cisco hosts will be saved in a scan.log file in the tool directory. Surely, you can specify any IP range for scanning and combine scanning with a dictionary attack on the fly ( -b option). Machines with no telnetd running will not. Disable Telnet on Cisco Routers/Switches. Let's see first how to disable Telnet on a Cisco IOS device which covers both Routers and Switches. Each Telnet access to the device (same applies with SSH as well) uses one of the VTY lines (Virtual Terminal lines). Crack adobe acrobat x pro serial number.
That is all ! You successfully recovered the password of your Cisco router !
If you have a Synology NAS and had some sort of disk crash in the past, you've probably encountered the famous 'Cannot format system partition' and 'Please configure your router to forward port 23 to DiskStation and contact Synology online support'.
Yeah, it sucks.
- The program attempts to open a connections to the telnet port (23) of random ips, if it succeeds the program logs the success in a log file telnet.txt for later analysis. The program then repeats, so if you run a few instances of the program for a few hours you can end up with a list of around 200 telnet boxes.Originally the program is written.
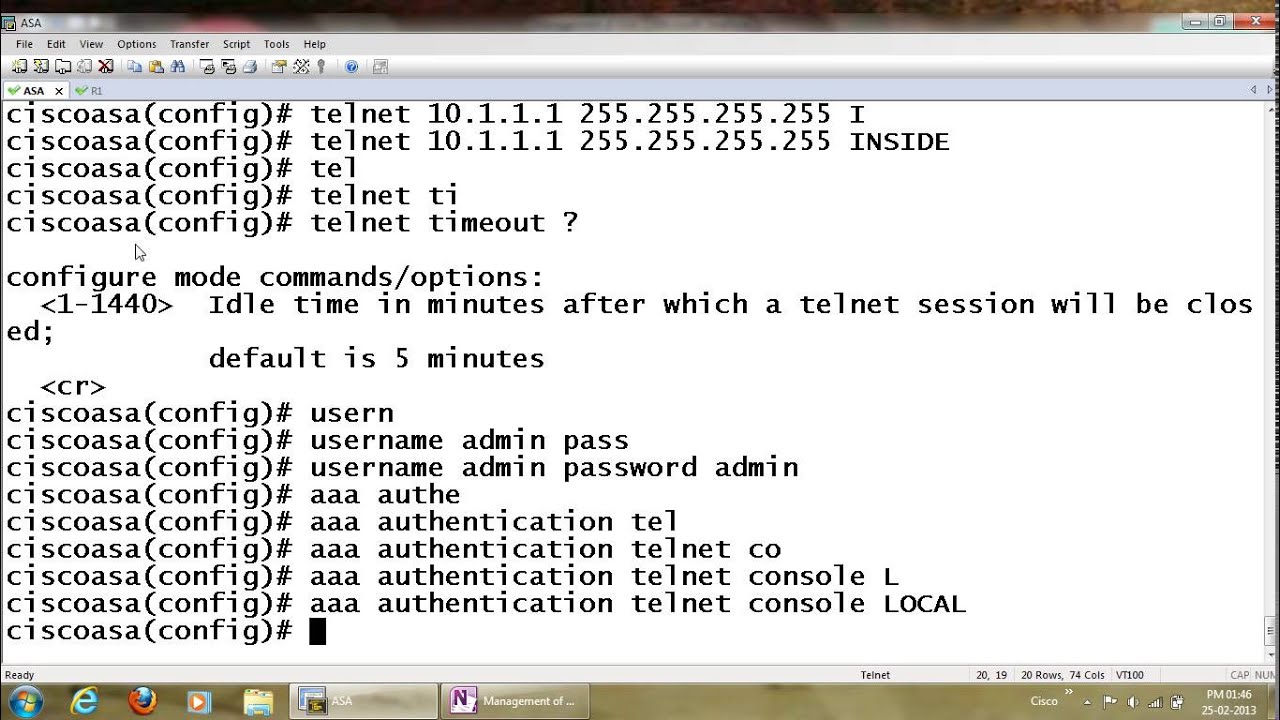
- Follow these steps to configure console passwords. Note: Before performing this test, ensure that you have an alternate connection into the router, such as Telnet or dial-in, in case there is a.
It sucks even more when you know the disk is perfectly fine, and you still have hopes to recover your data. Or you simply don't like the idea of having your port 23 open to the world for god-knows-how-long until a Synology tech support can look into your case.
You've probably tried telneting to your NAS. Maybe you've even tried opening the case and hacking the serial port, only to discover that you don't have the root password. The DS Assistant password doesn't work, and you exhausted all obvious guesses - blank, synopass, synology, password, admin, root, etc.
Well, what about c12-0804? No, I didn't make this up. This is today's password.
But if you're reading this a few days (or years) from now, too bad; it won't work. Unless, of course, you wait until December 8th. Because the password repeats every year.
Basically Synology hardcoded a modified login binary within the firmware that accepts an obfuscated password for root, which depends on the current date. (by the way, this isn't the only thing Synology folks hardcoded in the firmware).
Thanks to GPL, Synology was forced to publish the original source code for the firmware. Based on the original correct_password.c code, I hacked a short snippet to generate the daily password.
Here's the Synology Telnet password generator:
Compile and run the code above with gcc. You can also use the excellent CodepadRepl.it to run the code online and get the password for today (no registration needed).
Bonus tip: if you're curious how exactly the password is generated, here's the algorithm:
- 1st character = month in hexadecimal, lower case (1=Jan, .. , a=Oct, b=Nov, c=Dec)
- 2-3 = month in decimal, zero padded and starting in 1 (01, 02, 03, .., 11, 12)
- 4 = dash
- 5-6 = day of the month in hex (01, 02 ., 0A, ., 1F)
- 7-8 = greatest common divisor between month and day, zero padded. This is always a number between 01 and 12.
So, let's say today is October 15, the password would be: a10-0f05 where a = month in hex, 10 = month in decimal, 0f = day in hex, 05 = greatest divisor between 10 and 15).
If you have trouble calculating the greatest common divisor (elementary math, anyone?), Wolfram Alpha is your friend.
This was tested on a Synology DS212+, with Marvell Kirkwood mv6282 chipset. It's unlikely but still possible that different models use a different algorithm. YMMV, so always check the source code.
Hack Cisco Router Password Telnet Port 1
[UPDATE 1: Several users reported that this works in many other models, including DS409, DS112j, etc. Please leave a comment with your model and firmware version.]
Cisco Set Telnet Password
[UPDATE 2: If it doesn't work, it's probably that your date is incorrect in the NAS. Per Patrick's suggestion below, try '101-0101', which is the password for Jan 01]
